Preface
Azure Virtual Network Manager (AVNM) is a network management solution, released as public preview on November 02, 2021. Read the announcement here.
It aims to simplify the process of virtual networks creation, establishing peering among these VNETs and secure / govern these VNETS using global security rules, in combination with Network Security Groups (NSG).
What will be covered in this post?
- What are the challenges or problem scenarios which Azure Virtual Network Manager is aiming to solve?
- How AVNM solves these problems.
- Important Considerations about AVNM
- Known Limitations
- Licensing and Pricing
- Step-by-Step deployment and configuration of AVNM
- Conclusion
Challenges / Problem Scenarios
Whether an organization is Enterprises or medium scale, as far as it has a workload hosted on Azure, it must need an Azure Foundation including one or more landing zones compromising of one or more Virtual Networks. Virtual Networks are one of the most essential (if not the only) component deployed on Azure. Literally, every single Azure tenant has it!!
Use case A general use case is to deploy Azure Virtual Networks is hosting the Azure Virtual Desktop infrastructure or core infrastructure for integrating with Windows 365 Enterprise. Read my post blog on Windows 365 and Azure Virtual Desktop to know more.
Although deployment of virtual networks is a quick task, however proper planning and deployment of associated components such as Network Security Groups (NSGs), Virtual Network Peering etc. and finally establishing network security rules is quite cumbersome tasks and difficult to test, diagnose, and fine-tune.
Situation become more complex when enterprise organizations have multiple subscriptions across multiple regions, with segmented networks interconnected for distributed or isolated workloads. Usually such a distribution requires lots of management across network access and communications which is generally managed using combination of Network Security Group and Azure Firewall (or marketplace firewall running as Network Virtual Appliance (NVA)).
Managing such environment becomes a tedious and time-consuming task as every change to network access rules must be thoroughly evaluated as a change may negatively impact the overall posture and may leave an unwanted door opened mistakenly. And identifying it is a real challenge.
This is a challenge well understood and experience by Managed Services Providers (MSPs) who are managing customer’s Azure tenant and are responsible for day to day changes and operations across Virtual Networks.
How Azure Virtual Network Manager solves this problem?
This is where Azure Virtual Network Manager should add value by providing a centralized and simplified network management across subscriptions (globally). It is the place to manage your network resources, at scale, from a single plane of glass.
As listed on AVNM’s product page (here and here), following are the prominent features:
Feature: Global management of virtual network resources across regions and subscriptions
This helps to decrease the operational overhead on (creating and) managing the complex network topologies, as well as its security posture globally across subscriptions, within a tenant.
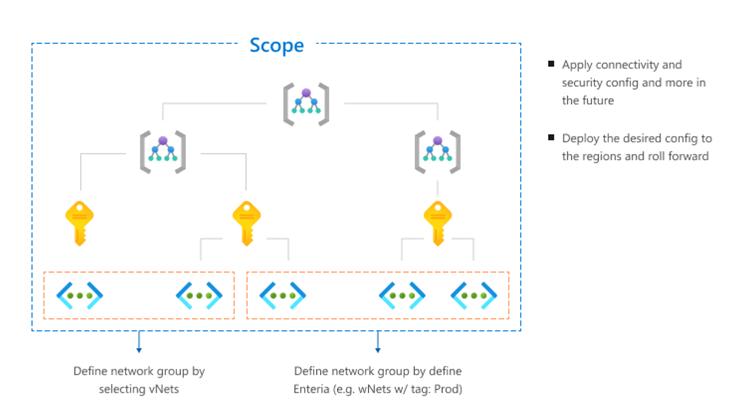
Note: Cross tenant management is not yet supported. Hence all the network resources across regions and subscriptions must exist within a single tenant.
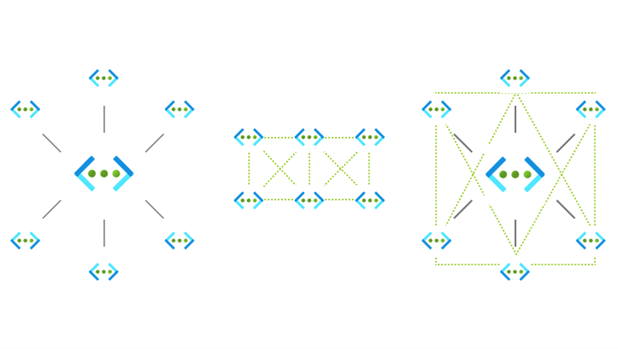
Feature: Automated management and deployment of virtual network topologies such as hub and spoke and mesh
This feature will be of great importance for the organizations who are continuously evolving/expanding and have already enable AVNM on their tenant.
Note: Azure Virtual Network Manager is currently in public preview. This preview version is provided without a service level agreement, and it’s not recommended for production workloads.
With this feature, organizations can deploy the VNET topology(ies) right from AVNM, rather than creating all VNETs one by one and then connecting/organizing them manually.
Use case As an IT security manager you can create different network groups to meet the requirements of your environment and its functions. For example, you can create network groups for Production and Test network environments, Dev teams, Finance department, etc. to manage their connectivity and security rules at scale.
Feature: High-priority security rule enforcement at scale to protect your network resources
This is probably the most interesting feature for network / security experts as it provides an overall and enforced-protection-layer to the organization’s virtual network.
The Global Network Security Rules (created using AVNM) can override and ensure protection even if there is a gap left open during the network rules configuration on NSG level.
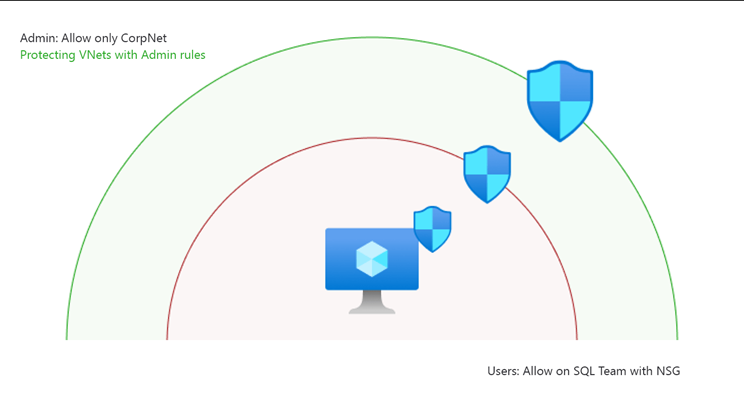
Use case • You can deny high-risk traffic: As an administrator of an enterprise, you can block specific protocols or sources that will override any NSG rules that would normally allow the traffic. • Always allow traffic: You want to permit a specific security scanner to always have inbound connectivity to all your resources, even if there are NSG rules configured to deny the traffic.
Feature: Simple deployment of network configurations
- It allows you to roll out network changes through a specific region sequence and frequency of your choosing.
- Enable transitive communication between spokes in a hub-and-spoke configuration without the complexity of managing a mesh network.
- Low latency and high bandwidth between resources in different virtual networks using virtual network peering.
Use case You can apply connectivity configurations to create a mesh or a hub-and-spoke network topology for a large number of virtual networks across your organization's subscriptions.
For more detail on use-cases, refer to link here
Important Considerations
- AVNM is currently in public preview which is not recommended to be deployed in production environments.
- Azure Virtual Network Manager is currently available in US West, US West2, US East, US East2, and US North Azure regions (reference link)
- AVNM is natively highly scalable service (with redundancy and replication across the globe). Hence no manual efforts are required to comply for its SLA.
- A virtual network can belong to more than one Azure Virtual Network Manager instance.
- Appropriate permissions (network contributor) is required to access and manage required virtual networks, from another subscription.
Limitations
- A hub in a hub-and-spoke topology can be peered up to 250 spokes.
- A mesh topology can have up to 250 virtual networks.
- The subnets in a virtual network can’t talk to each other if they have the same address space in a mesh configuration.
- The maximum number of IP prefixes in all admin rules combined is 1000.
- The maximum number of admin rules in one level of Azure Virtual Network Manager is 100.
- Azure Virtual Network Manager doesn’t have cross-tenant support in the public preview.
- A virtual network can be part of up to two mesh configurations.
- Cross tenant management is not yet supported. Hence all the network resources across regions and subscriptions must exist within a single tenant.
For more read on known limitations, refer to link here
Licensing and Pricing
Azure Virtual Network Manager is currently in public preview and free of charge.
It will start billing on Feb 1st, 2022 (probably this gives us an indication on when AVNM is planned to be Generally Available?)
Anyway, till Feb 1st, 2022:
- No upfront cost
- No termination fees
- Pay for only what you use
How to create an Azure Virtual Network Manager?
Before you start creating AVNM instance, you will need to enable your subscription for the preview feature.
Look for “Preview Features” on the Azure Portal search bar:
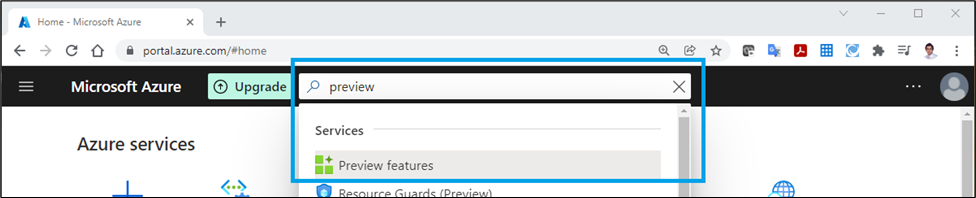
Search for “AllowAzureNetworkManager”, select and click on “+ Register” button to register your subscription for this preview feature.
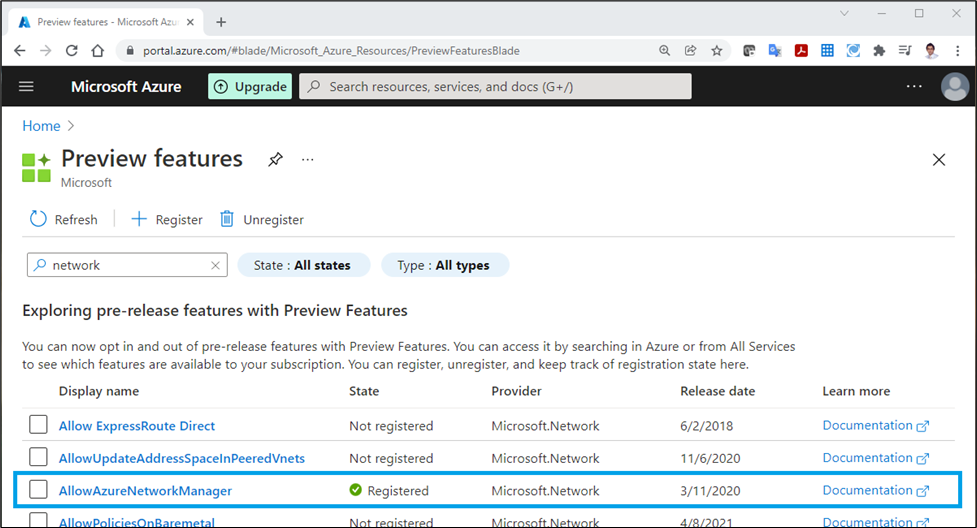
Once registered, go to “Network Managers” blade by searching on the Azure portal:
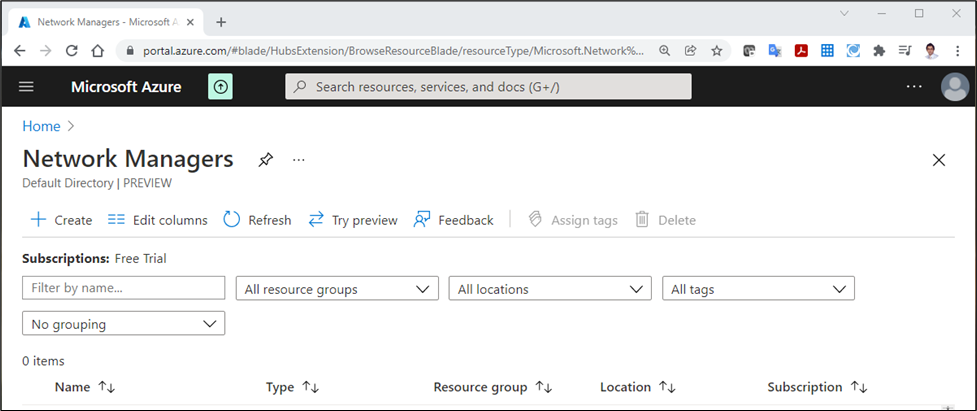
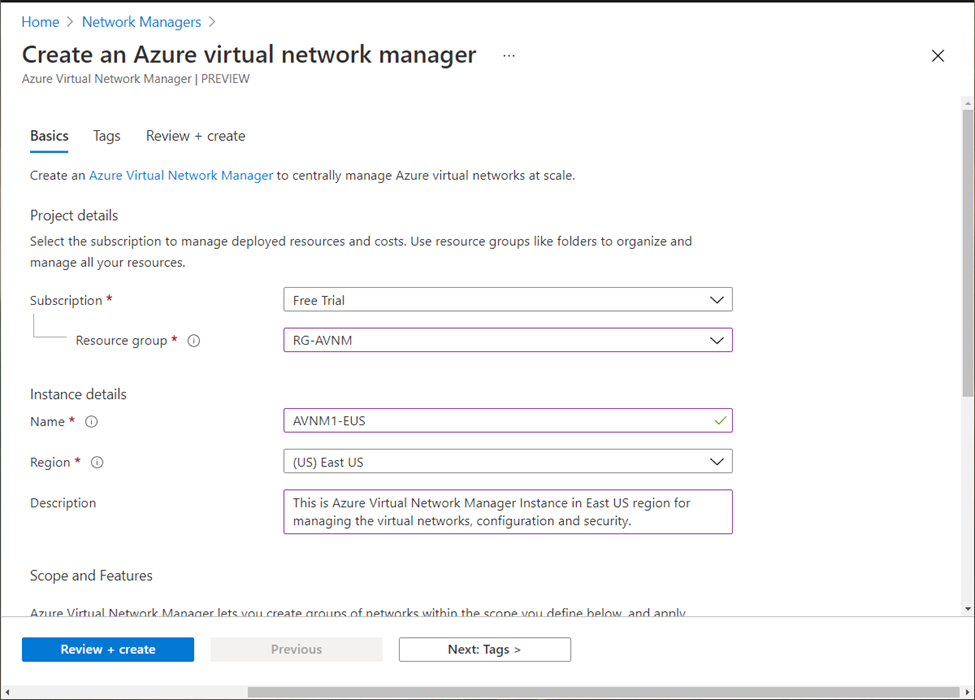
Create an Azure Virtual Network Manager Instance. You will need to provide following information:
- Select Subscription (I am using a free trial subscription for this blog).
- Resource Group name (where AVNM instance will be created).
- Provide Azure Virtual Network Manager Instance Name.
- Select required region for creating the AVNM instance (available regions are listed above).
- Provide a description for your record.
Select scope for the AVNM. This could be a Management Group or Subscription.
Select among the two features required “Security Admin” and “Connectivity” depending on your usage requirement for this AVNM instance.
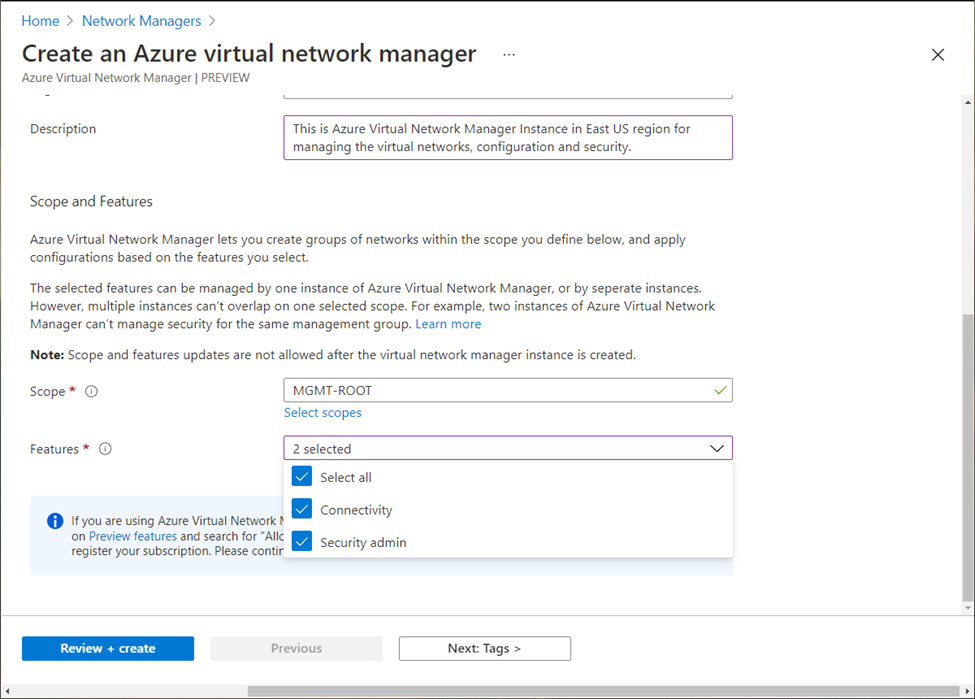
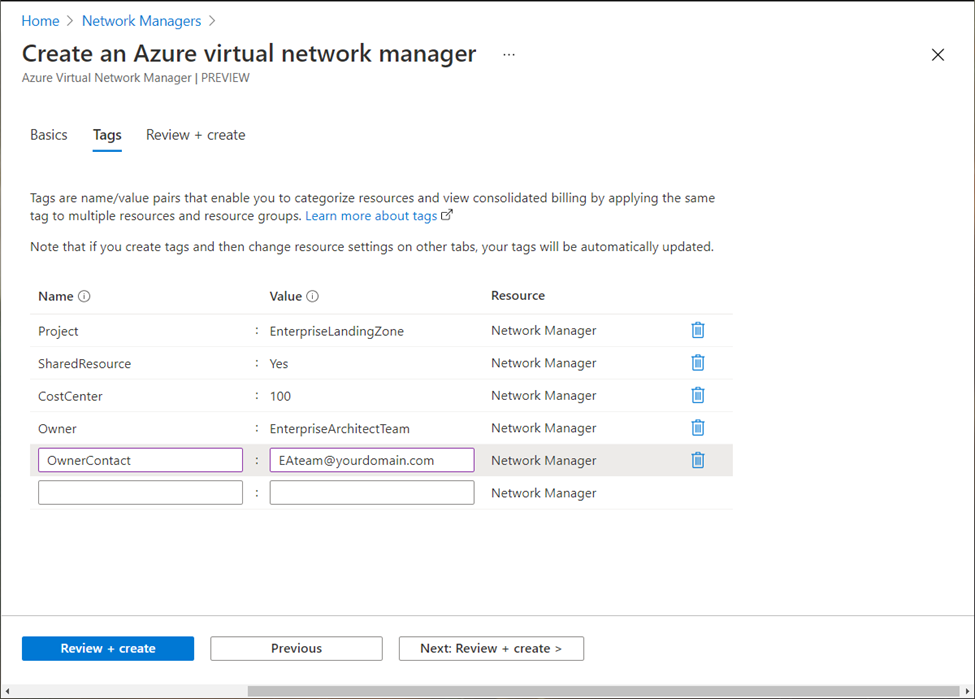
(Optionally) Add the required Tags to the AVNM instance.
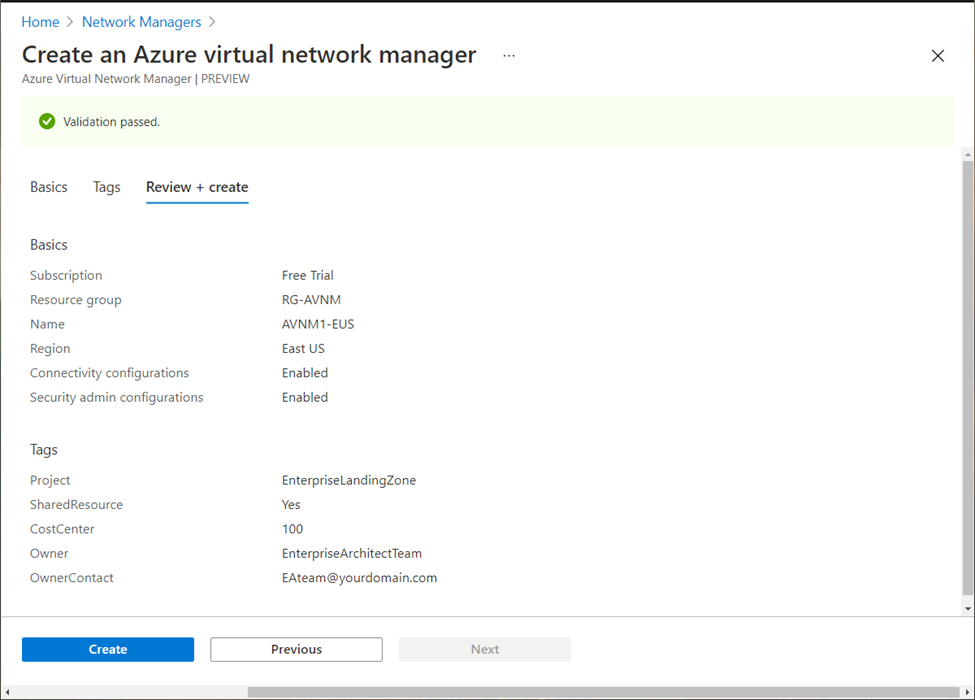
Review the provided configuration and values. Proceed for creation of AVNM instance:
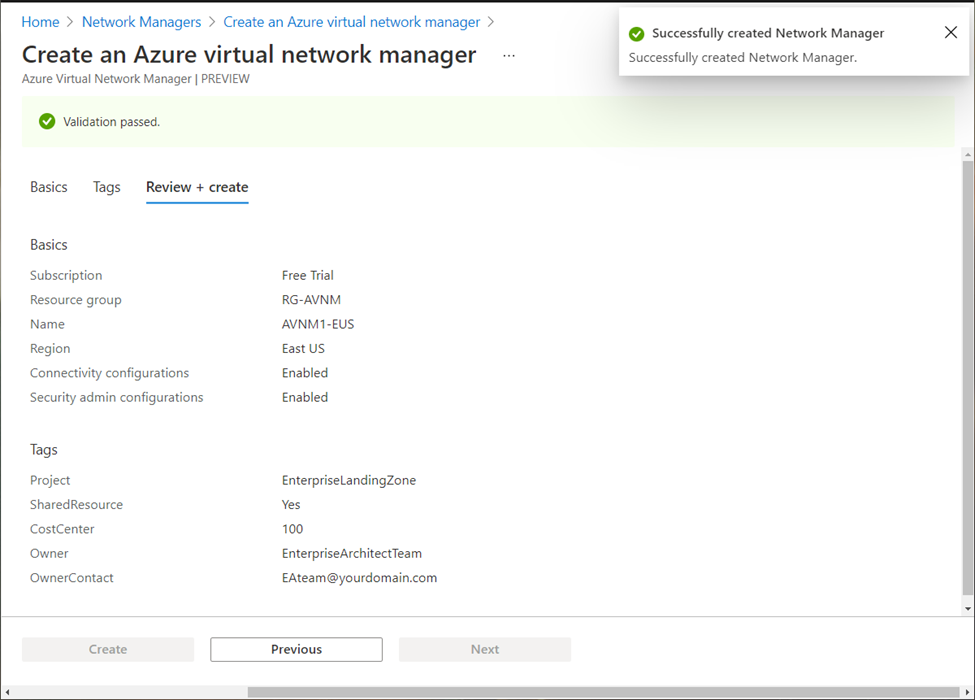
Once the instance is created and available for use (takes few seconds), you will be presented with following product blade:
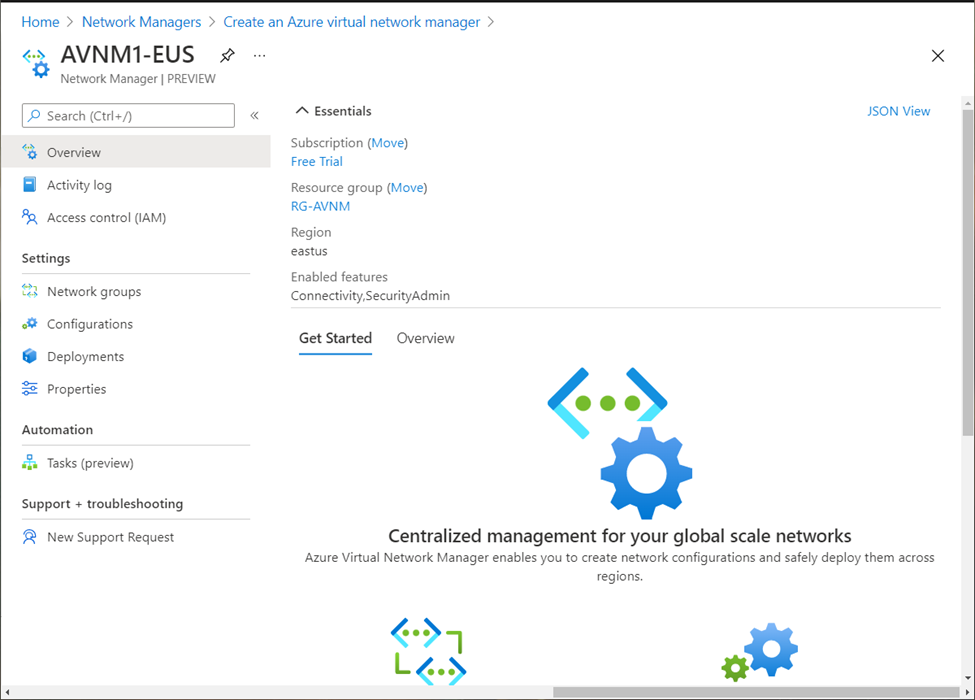
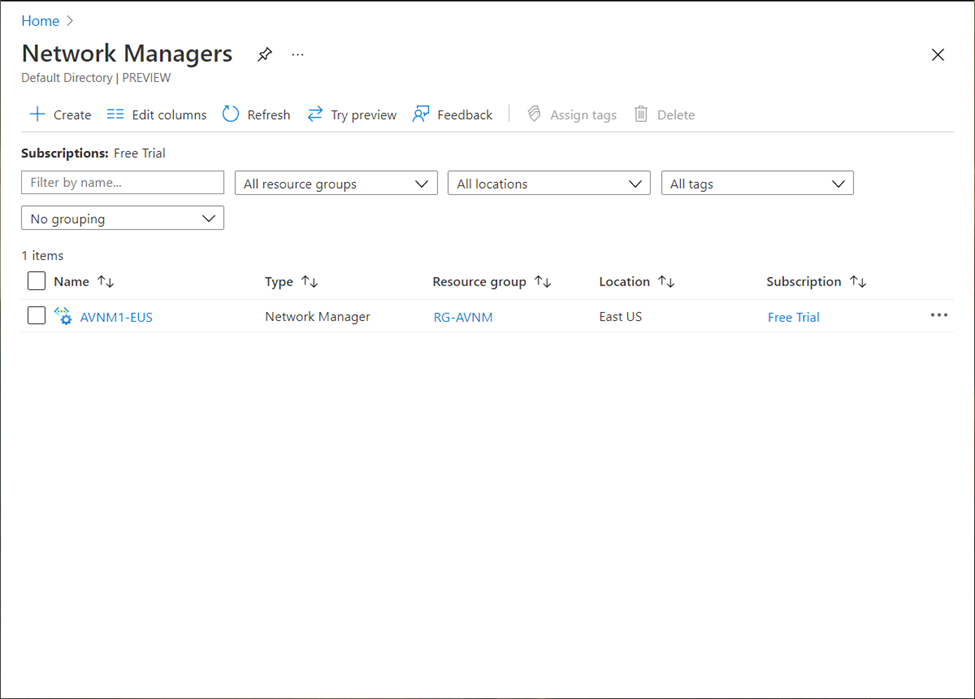
You may also browse to “Network Managers” from Azure Portal Search bar, to view all the AVNM instances in the organization.
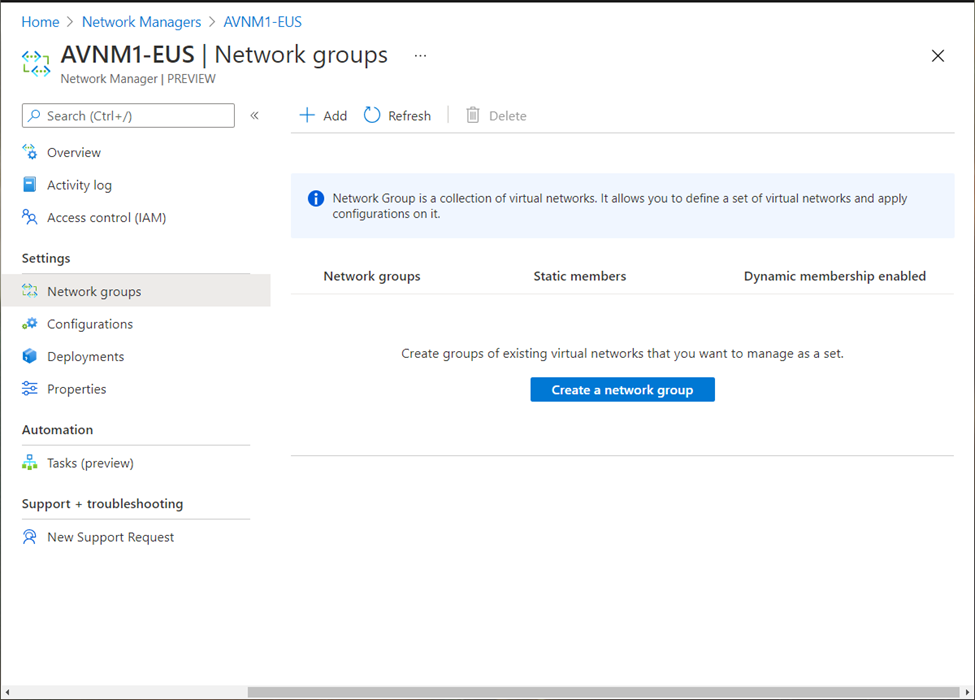
AVNM Network Groups
First thing to do is to create network groups. which is essentially a collection of virtual networks which will be managed using this AVNM instance.
While AVNM instance is selected, go to network groups and click on “+ Add” or “Create a network group” button.
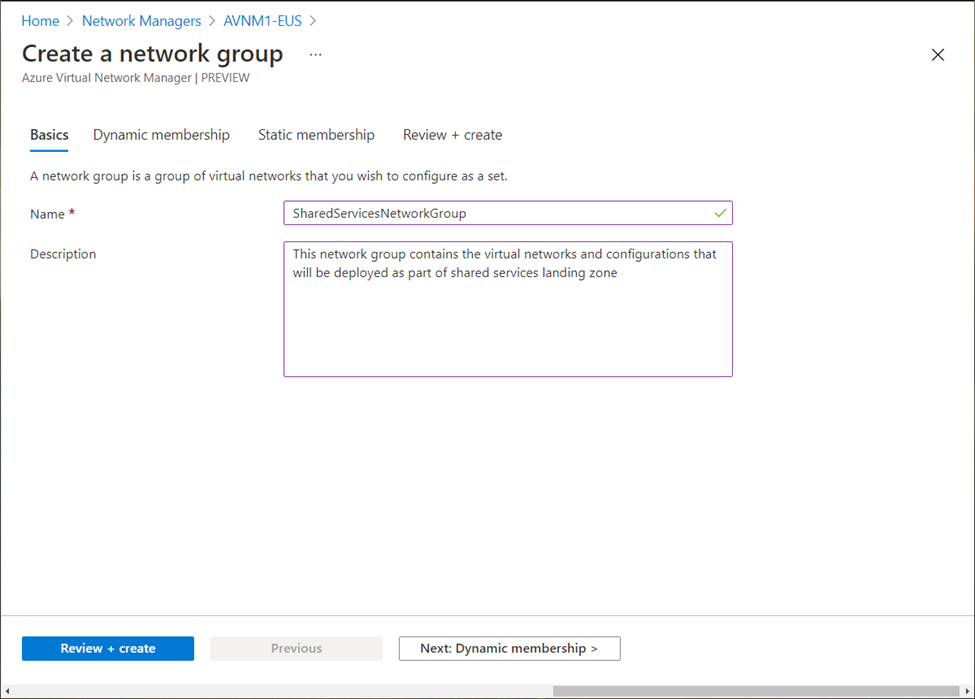
Provide Network Group name and description:
Here a dynamic criteria can be defined so that any virtual network created matching this criteria, will automatically come under management of this AVNM instance.
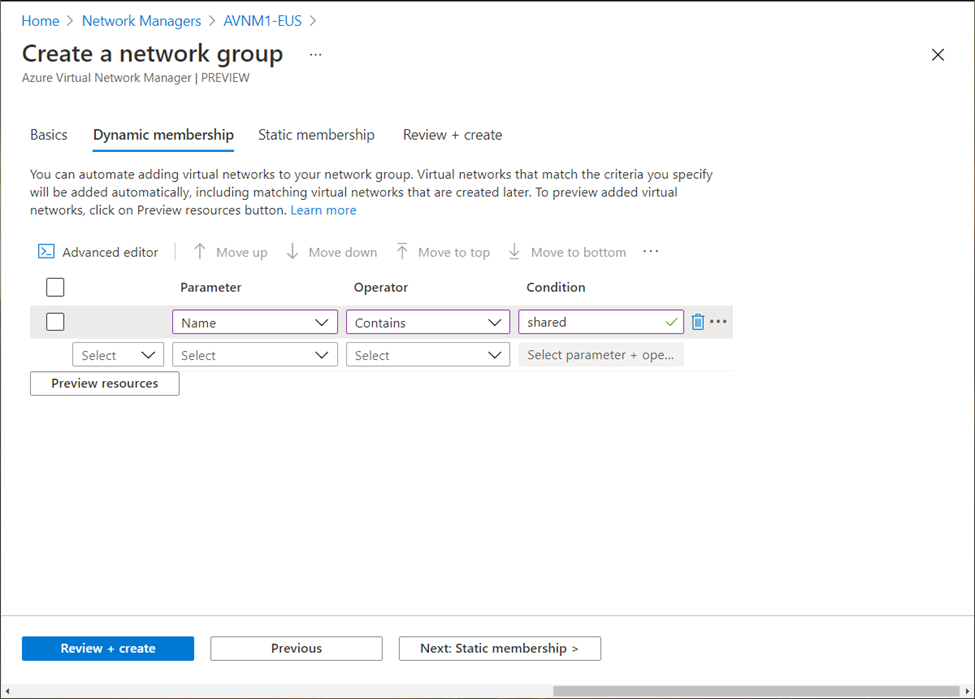
Or, virtual networks can be added manually as well:
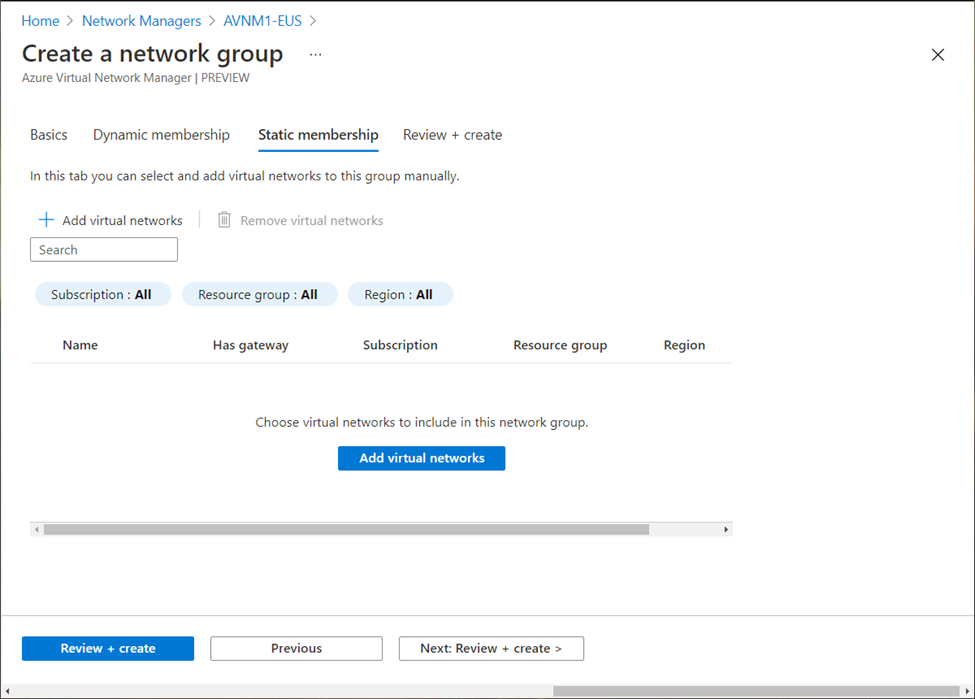
You can always review the configuration (and go back to change if required) before creating the network group.
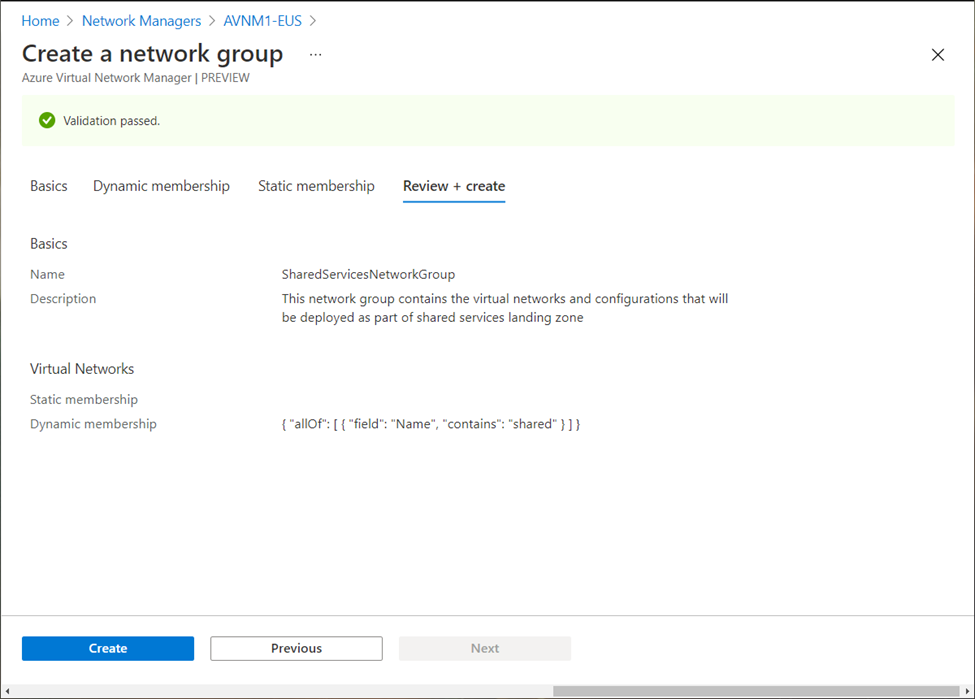
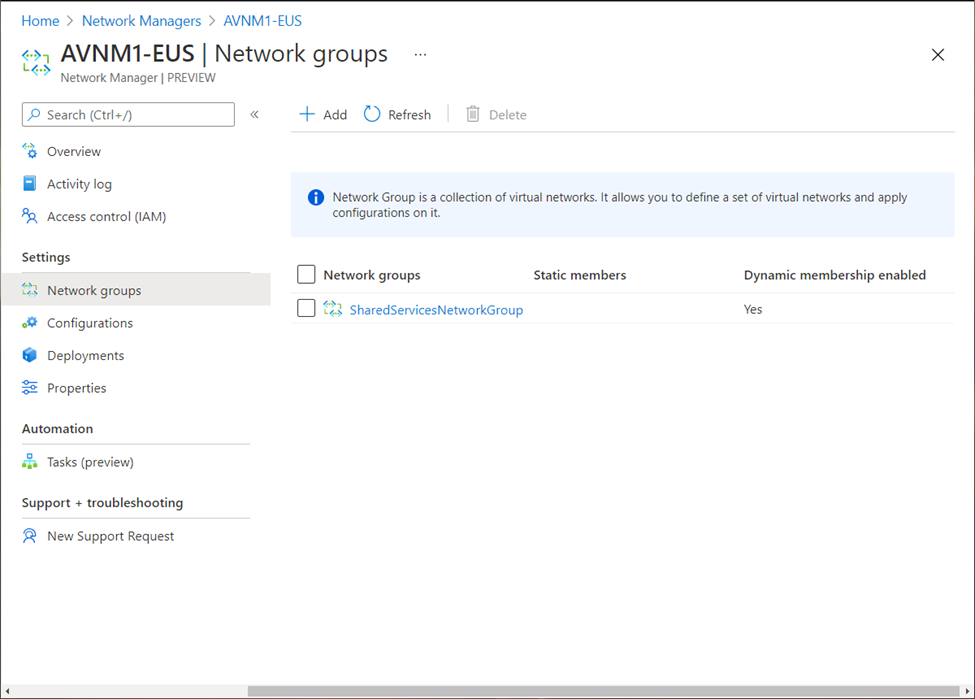
Network groups appear under respective AVNM instance and can be managed or modified any time.
AVNM Configurations
AVNM allows two types of configurations to be deployed on network groups (created above).
- Connectivity Configurations: which are mainly topology settings related to connectivity of managed virtual networks.
- Security Admin Configurations: which are mainly the security settings governing the managed-virtual-networks and respective network security groups.
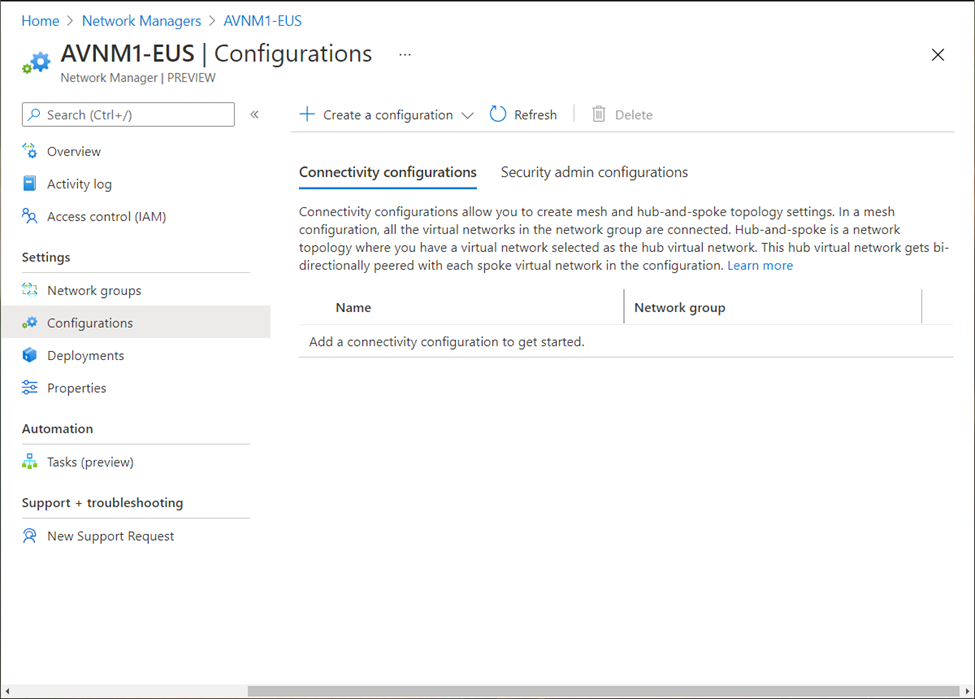
A connectivity configuration can be created to define if all the managed-virtual-networks (which are part of selected network group) should be connected in a Mesh topology or Hub and Spoke topology.
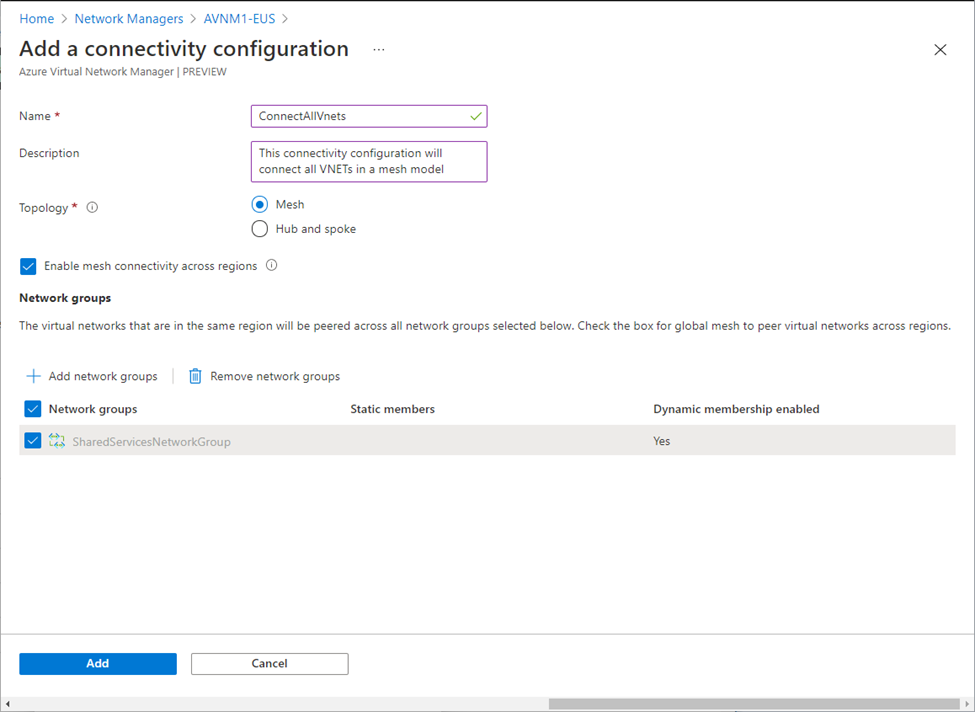
Similarly a security admin rule configuration can be created to define the global (security) admin policies which will eventually override the NSG rules create for the managed-virtual-networks. As an example, following rule will block port 3389 even if an NSG rule is configured to allow it.
This way, organizational security admins can enforce a standard policy and ensure that it is not violated.
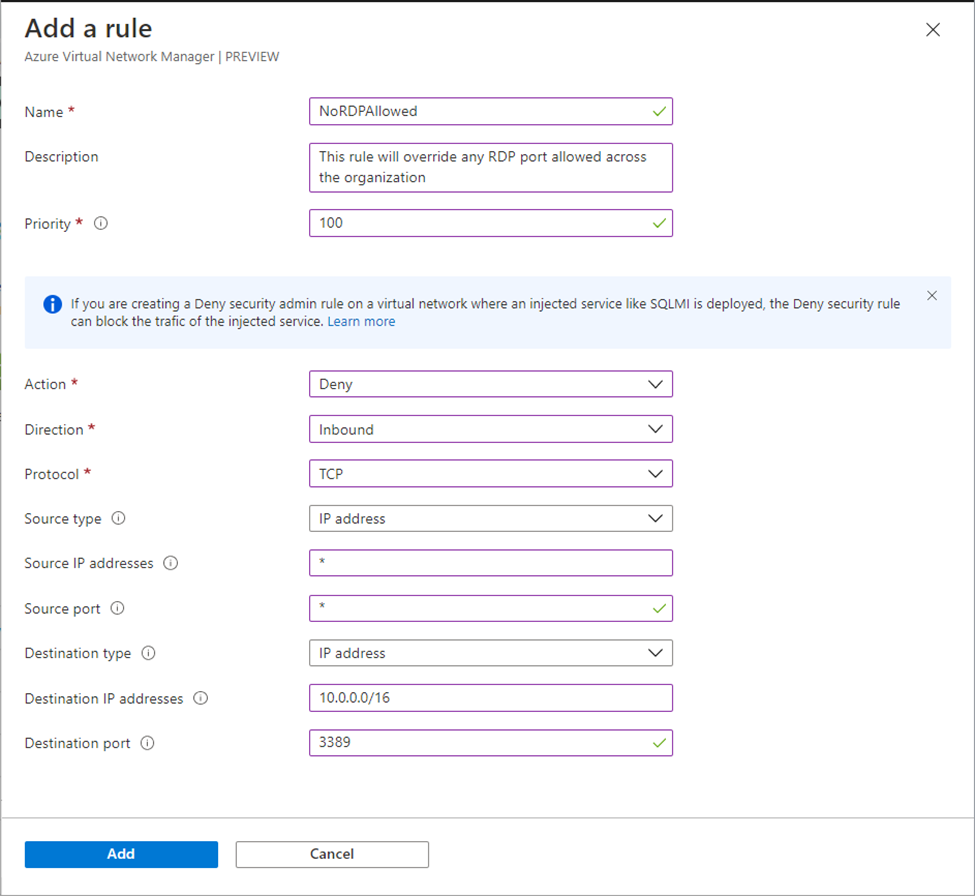
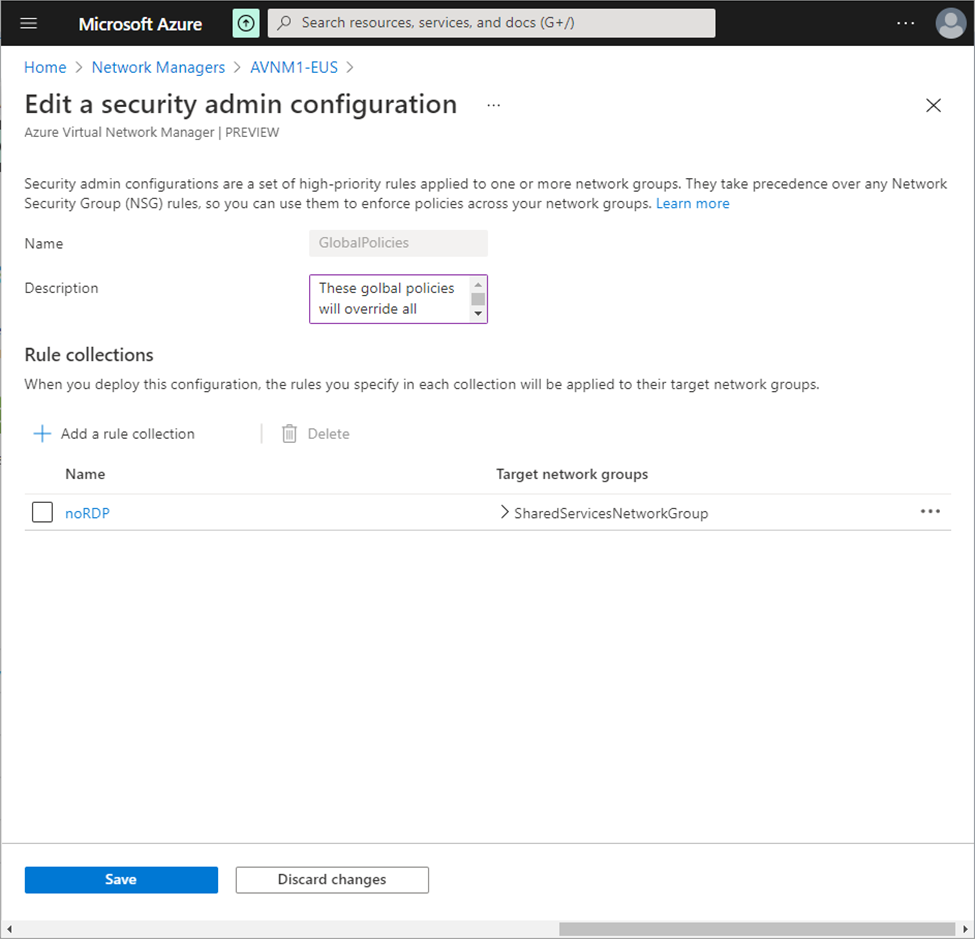
Multiple rule-collection can be added in a security admin configuration.
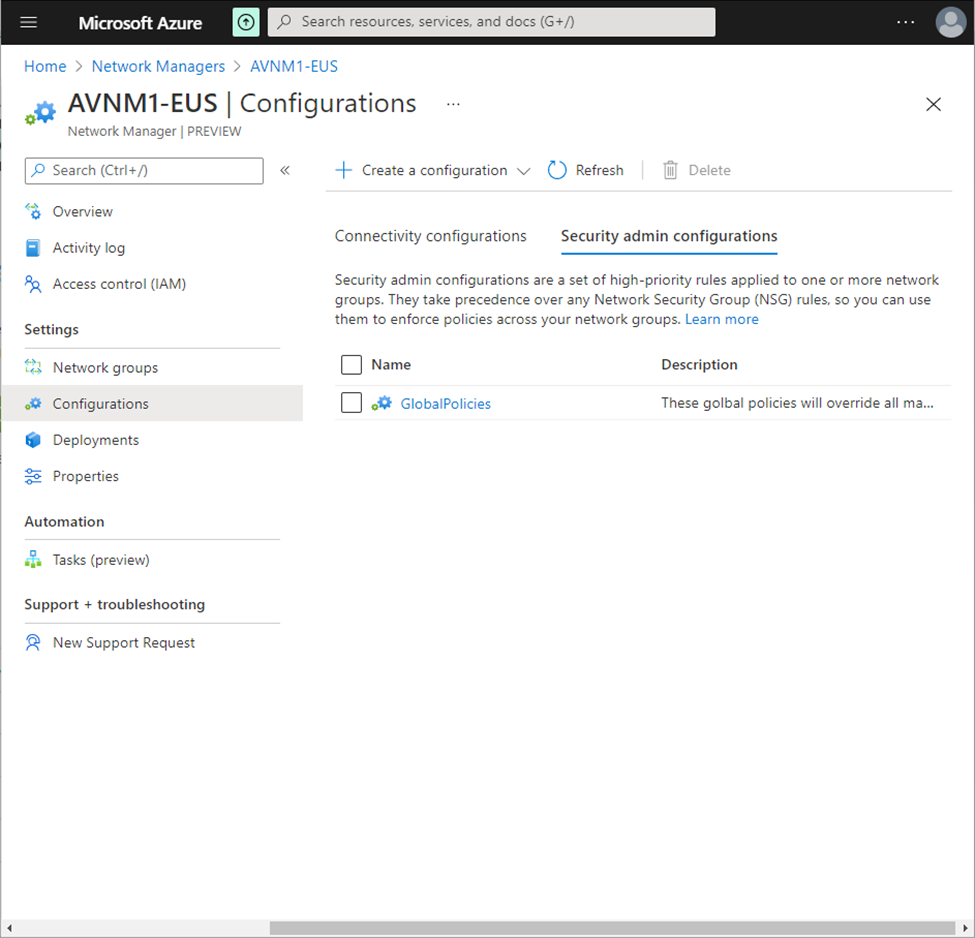
AVNM Configuration Deployment
Configurations, once configured, can be deployed to become effective, in selected regions.
For example: connectivity configuration deployment to East-US region:
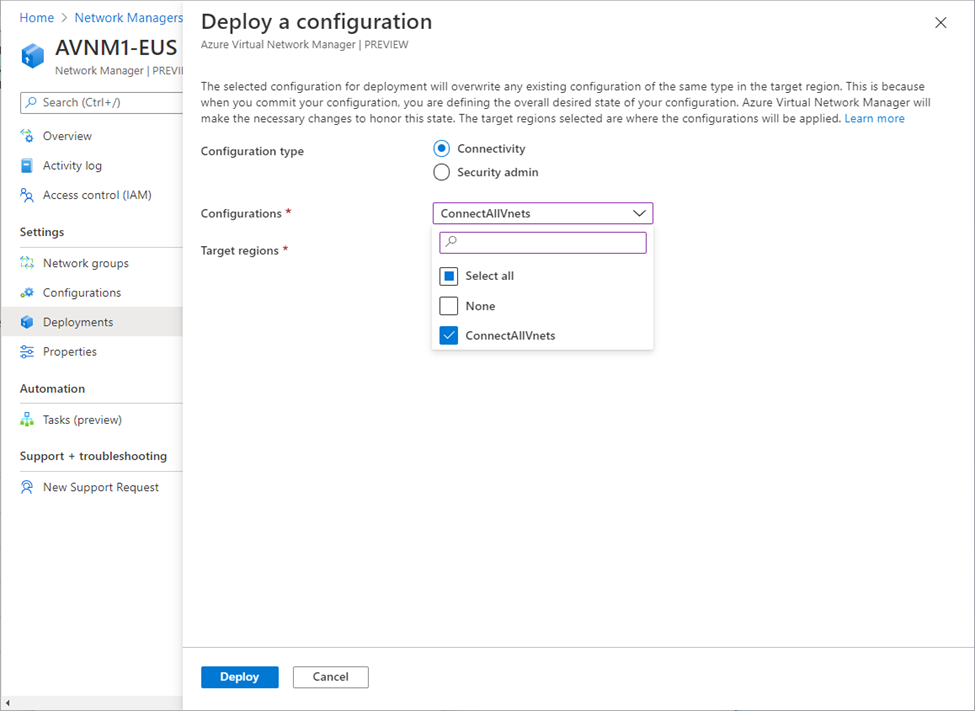
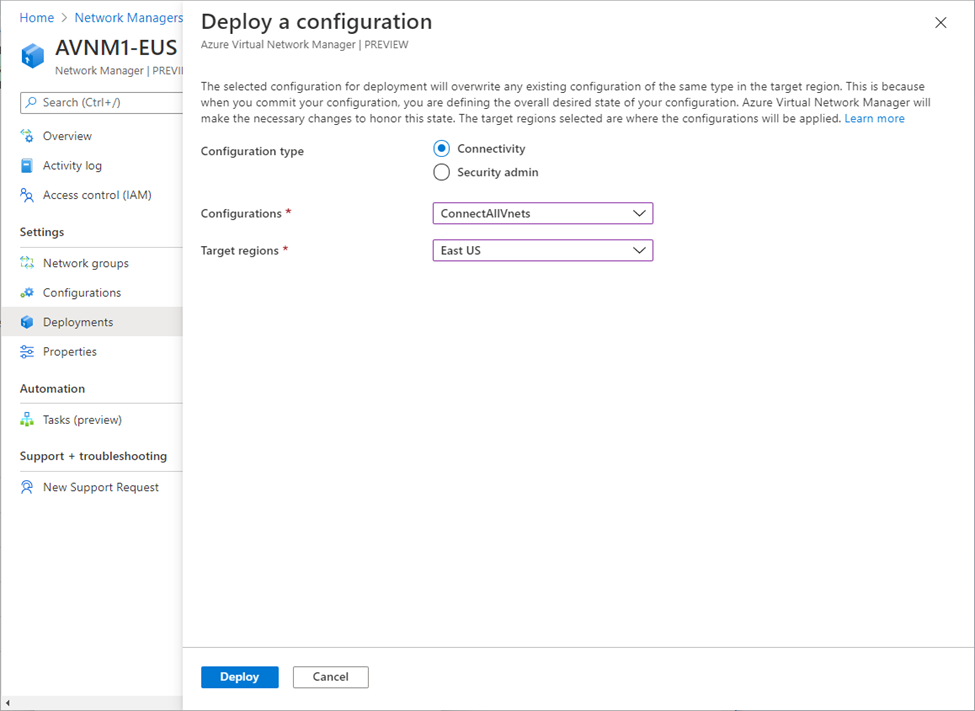
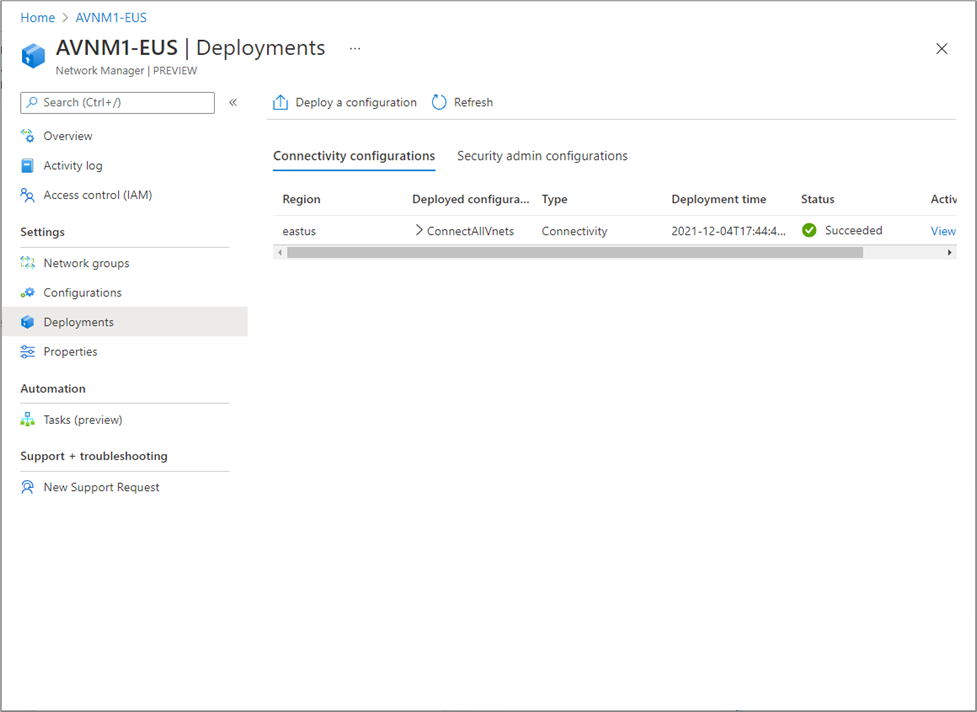
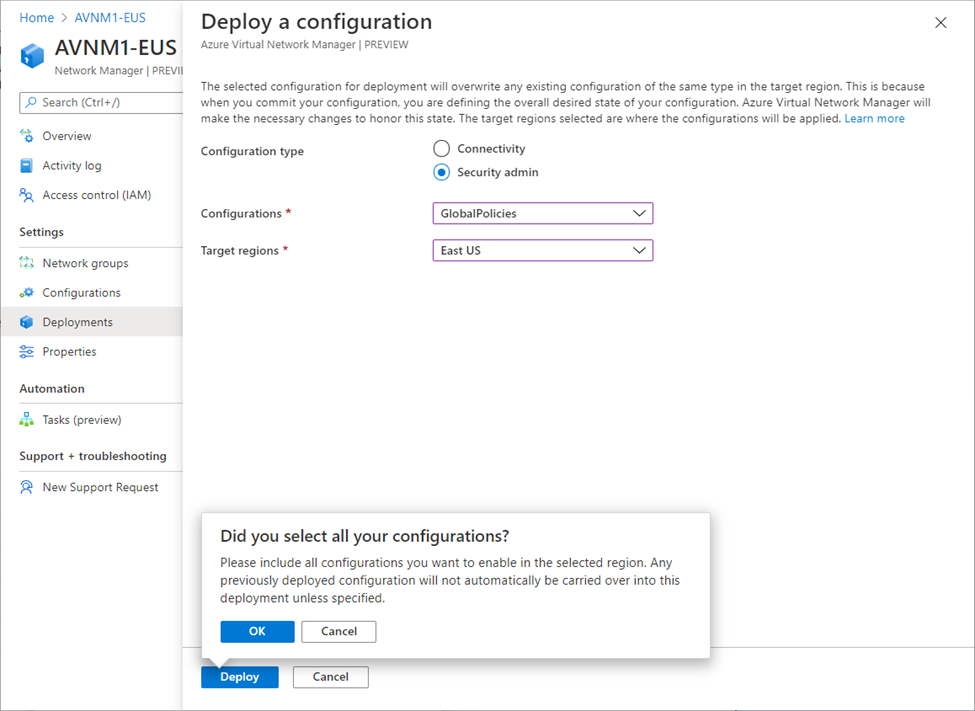
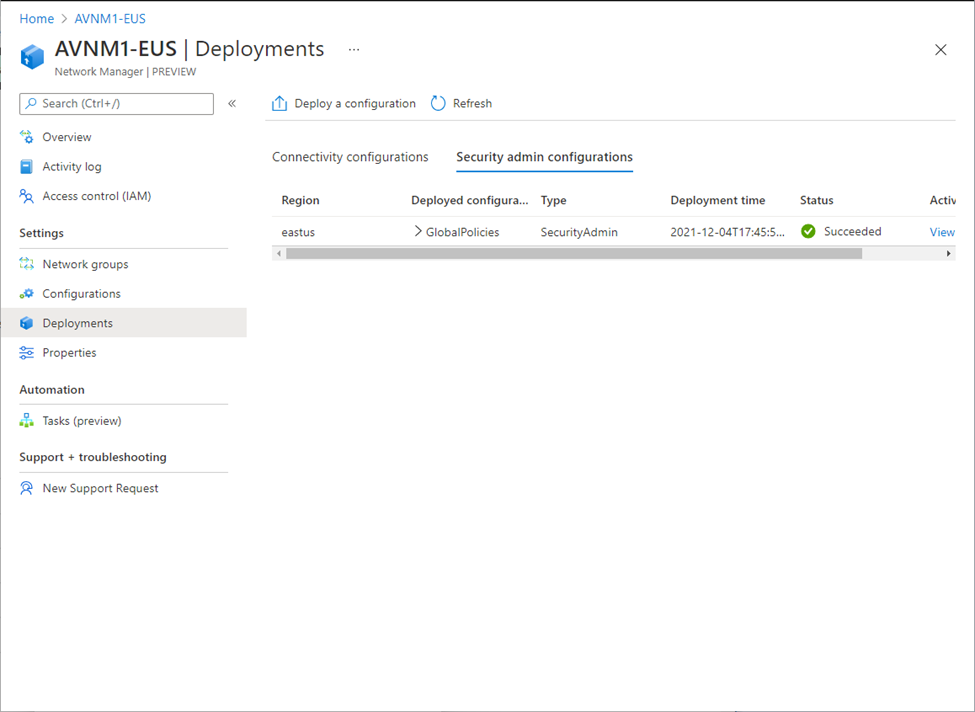
For example: Security Admin configuration deployment to East-US region:
Automation / Tasks:
You can also create automated tasks to run on a schedule. Such as generating a monthly report of resource cost
Conclusion
Azure Virtual Network Manager (AVNM) is a good solution for managing virtual networks as well as their connectivity and security configurations. It is in preview and comes as a free service until February 2022.
It will definitely be helpful for medium to enterprise organizations in reducing the overhead of creating VNETs and respective peering’s. Hence it will reduce the time required for VNET deployment and inter-connectivity.
As well as the Enterprise Cloud Architects and Security Admins can setup the baseline / standard security policies in place which remain effective and enforced throughout the lifecycle of the tenant operations.
Currently, it is limited in features (limited to virtual networks only) however, very likely we will have more and more features/capabilities announced in future. It would be so great if Application Security Groups (ASGs) and other network / security components i.e. Azure Firewall, Application Gateway can also be integrated into the management capability of AVNM.